Physical Address
304 North Cardinal St.
Dorchester Center, MA 02124
Physical Address
304 North Cardinal St.
Dorchester Center, MA 02124
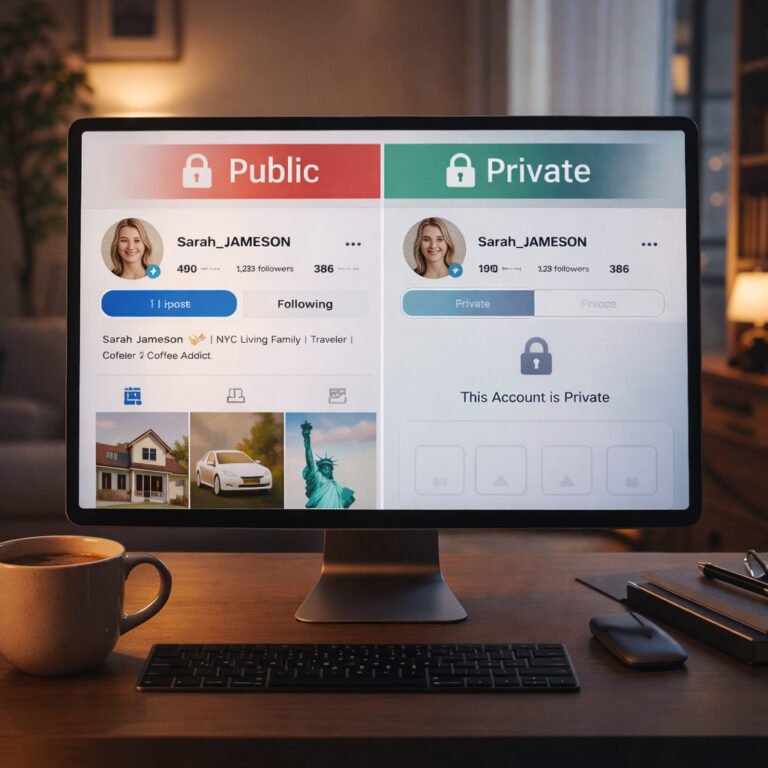
Private vs public social media is not a simple “one is safe, one is dangerous” question. In reality, both options come with trade-offs. A public profile can increase exposure, while a private profile can create a false sense of safety. The best approach depends on what you use social media for, what you share, and how much digital footprint you are willing to accept. In this guide, you’ll learn the…

How to use LinkedIn safely is a question more people should ask. LinkedIn is not just a “career platform” anymore — it is also one of the biggest OSINT databases on the internet. While Instagram and Facebook reveal your lifestyle, LinkedIn reveals something else: your identity, your workplace, your professional network, and your credibility. The problem is simple. Most people build their LinkedIn profiles to look impressive, not to be…
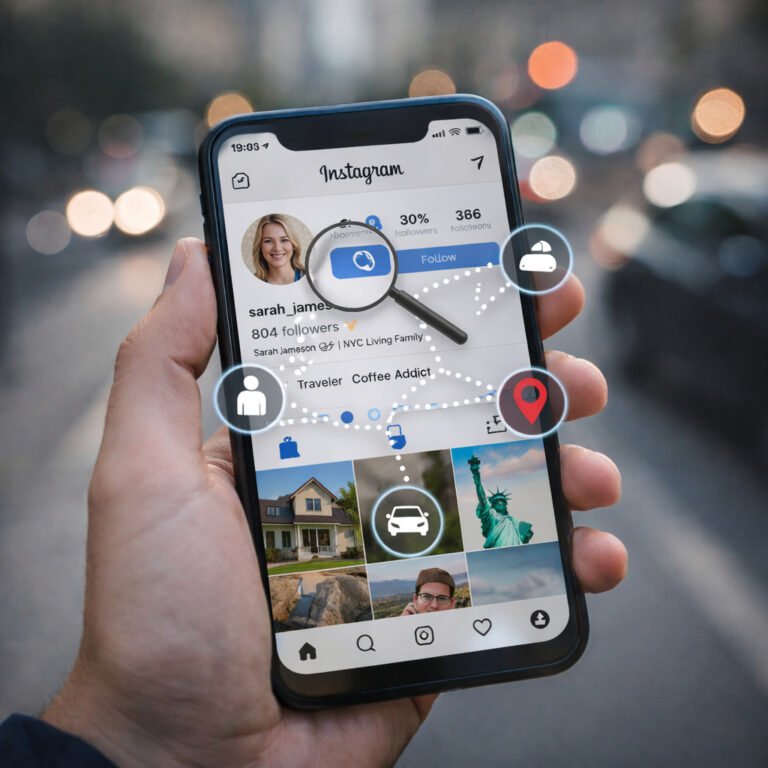
How criminals use social media is not a movie scenario — it’s a real-world OSINT technique used every day. Instagram and Facebook are not dangerous because of “hackers.” They are risky because people voluntarily publish patterns, locations, and personal details that can be connected into a full profile. In this guide, you’ll learn how criminals use social media in realistic ways, what information they look for, and how to reduce…

Why posting in real time is risky is not a paranoia topic — it’s one of the most practical online safety habits you can learn. The moment a Story, check-in, or “right now” post goes live, it may reveal your location, your routine, and even the fact that your home is empty. Because timing is data, real-time posting affects both personal safety and online privacy. In this guide, you’ll learn…

Posting a photo shouldn’t feel dangerous. However, in 2026, sharing pictures online can reveal far more than you think. If you care about online privacy security, this is one of the most important habits you can build. The good news? You don’t need to stop sharing your life. You just need to share smarter. In this guide, you’ll learn how location exposure really happens, what the most common mistakes are,…

Why Practical Cybersecurity Matters More Than Rules Protecting young people online is not about installing one app, blocking one website, or setting one rule. It is about building daily habits, shared responsibility, and realistic boundaries that work both at home and at school. Young people already live online. The question is not if they will face digital risks — but how prepared they are when it happens. This final article…

When Seeing and Hearing Is No Longer Believing Deepfake threats for young people are no longer science fiction.Artificial intelligence can now generate fake voices, images, and videos that look and sound real. What once required advanced technical skills is now accessible through simple apps and online tools. For young people who grow up trusting video calls, voice messages, and social media content, this creates a new challenge: how to know…

Why Scams Target Kids and Teens Online scams for kids and teens rarely look like “crime.”They look like messages, rewards, friendly chats, and opportunities that feel exciting, urgent, or exclusive. Children and teenagers are not targeted because they are careless. They are targeted because: This article explains how online scams and fake giveaways trick kids and teens, what patterns appear again and again, and how families can recognize scams early…

Why Games and Chats Are a Cybersecurity Risk Zone Cybersecurity risks for kids and teens are most likely to appear where young people spend the most time — online games, chat platforms, and social media. These spaces feel fun, social, and familiar, which is exactly why attackers, scammers, and manipulators target them. Games and social platforms are not dangerous by default. However, when communication, anonymity, and emotional triggers mix together,…

Cybersecurity Basics for Kids Start Earlier Than We Think Cybersecurity basics for kids are no longer optional — they are a modern life skill.Children and teenagers grow up online long before they fully understand privacy, trust, or digital risks. From online games and social media to school platforms and messaging apps, the internet is deeply embedded in everyday life. This article explains cybersecurity basics for kids and teens in a…